Turnkey Cybersecurity for End-Users
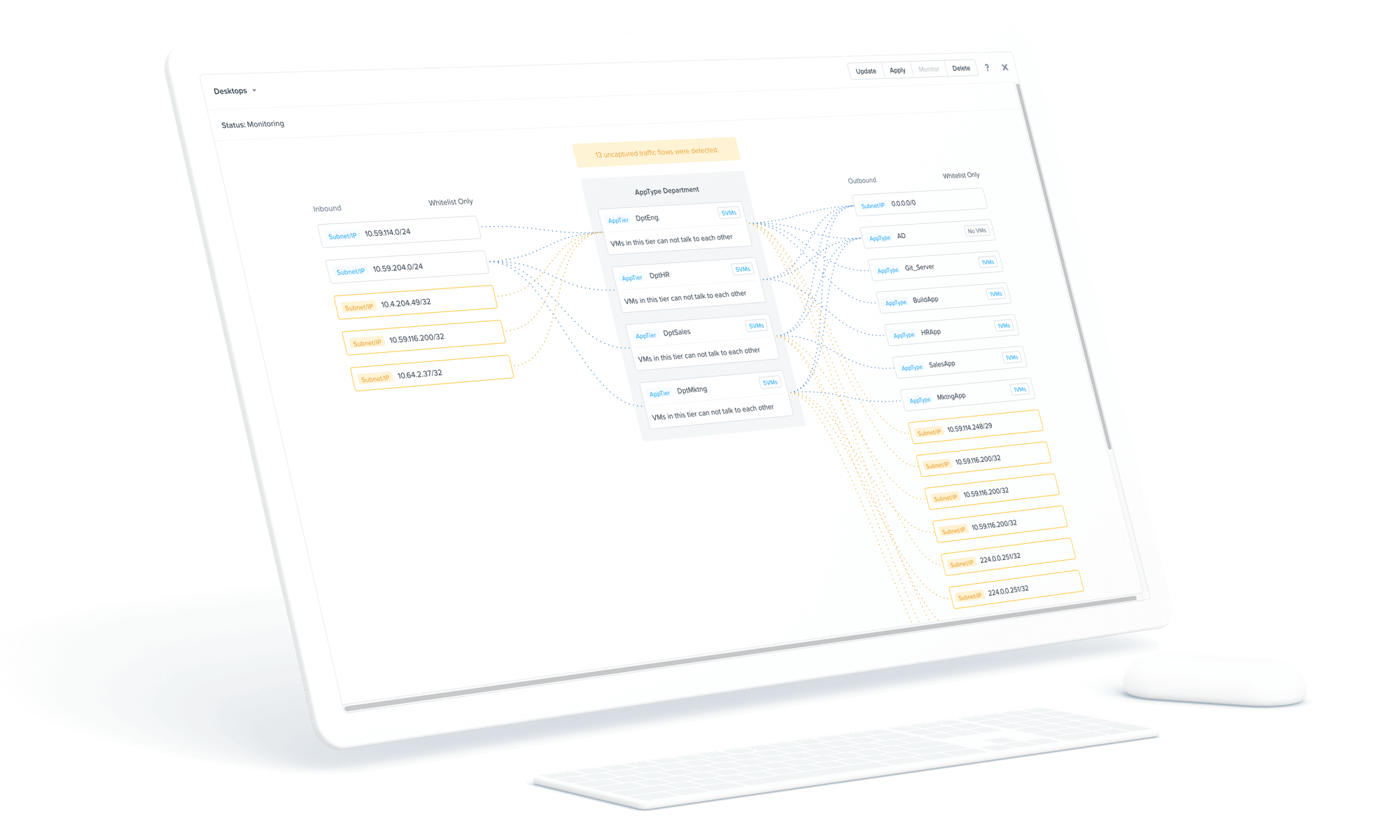
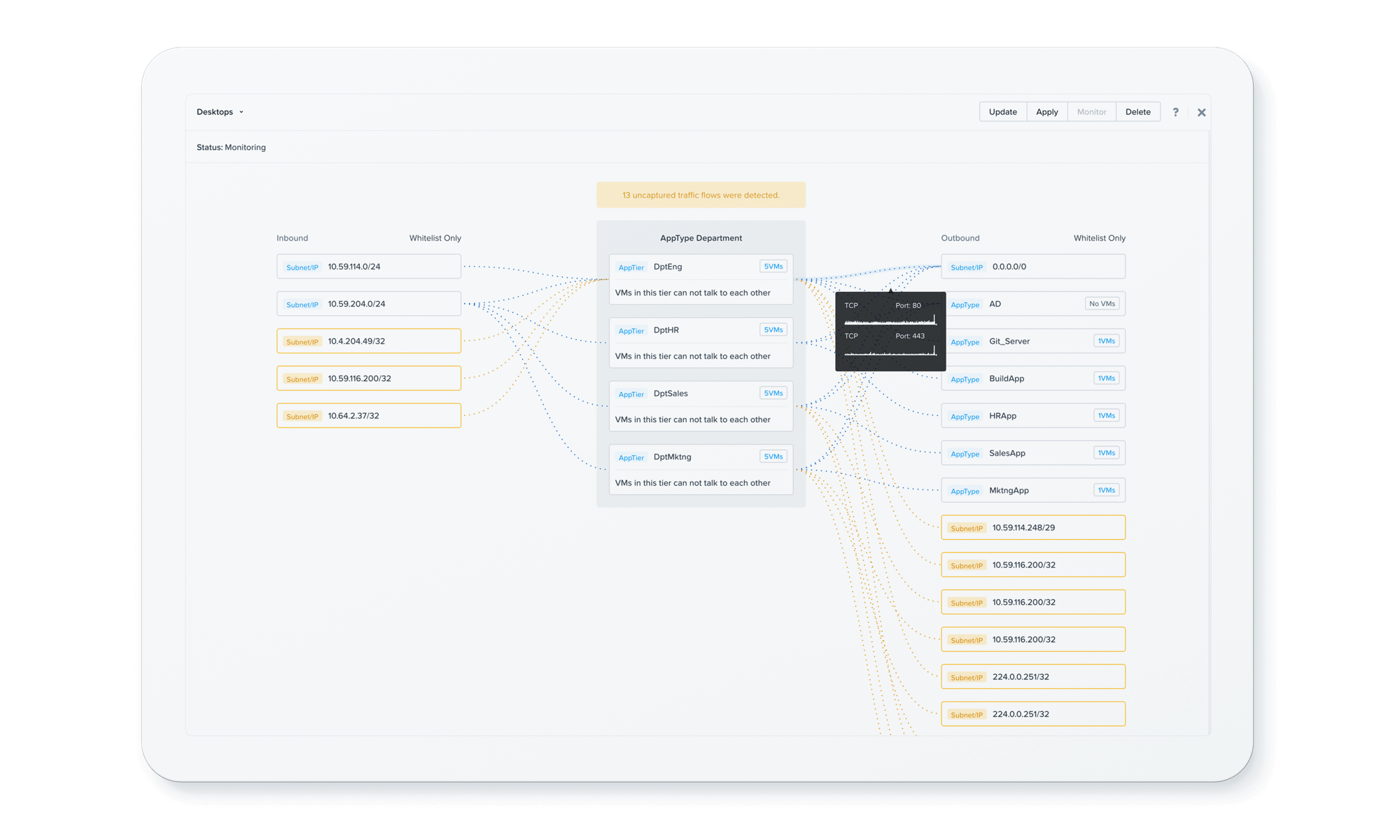
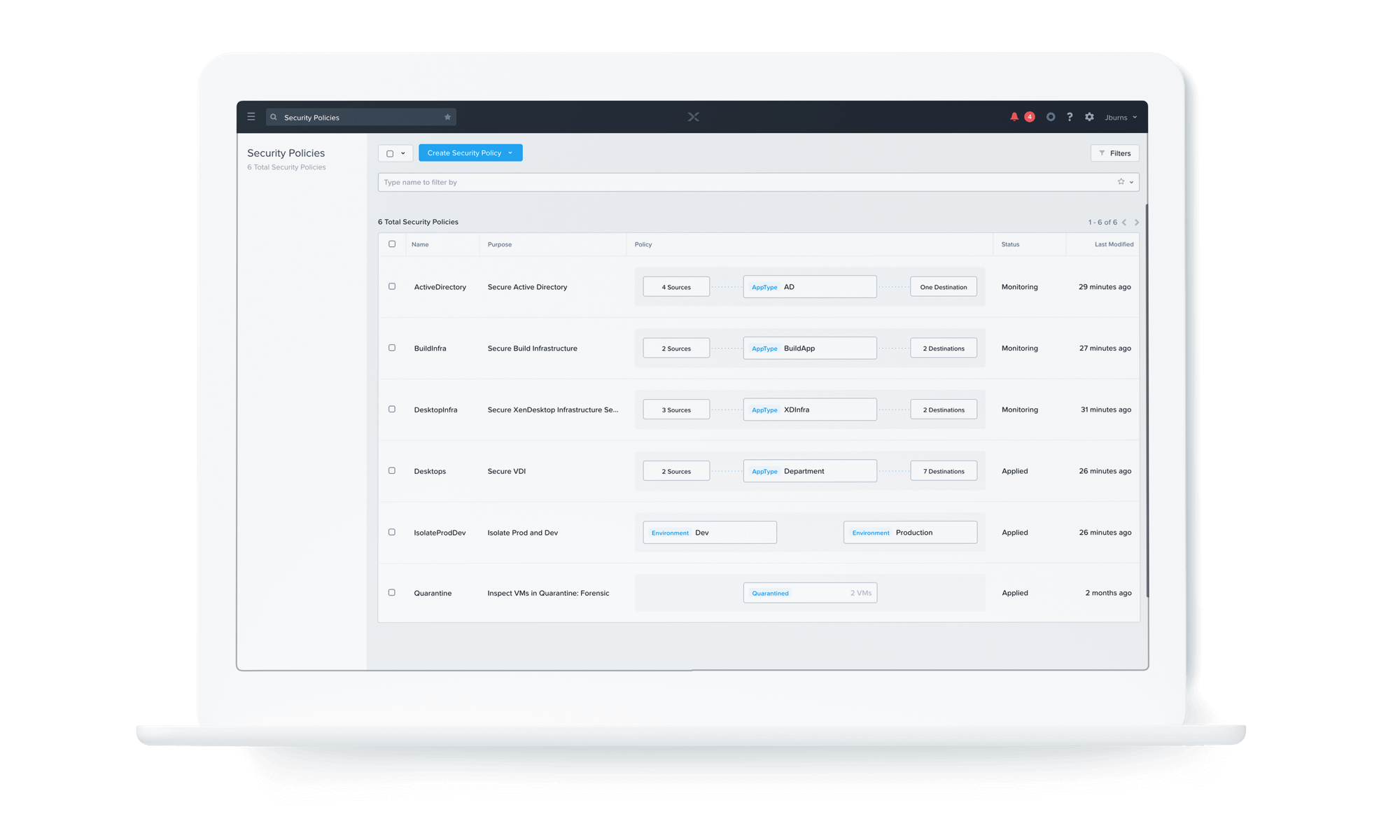
Understand application communication
Visually map new or existing application workflows at a port level to better control access or application communications.
User-centric identity and malware protection
Enhance end-user security by leveraging identity to control network access to workloads and data (directory-based) while blocking the spread of malware and ransomware with microsegmentation.
Ensure access compliance
Easily segment application and data access without physically managing and building compliant networks using ring fencing and audits.
Enteprise-Grade
Defense-In-Depth for Apps and Data
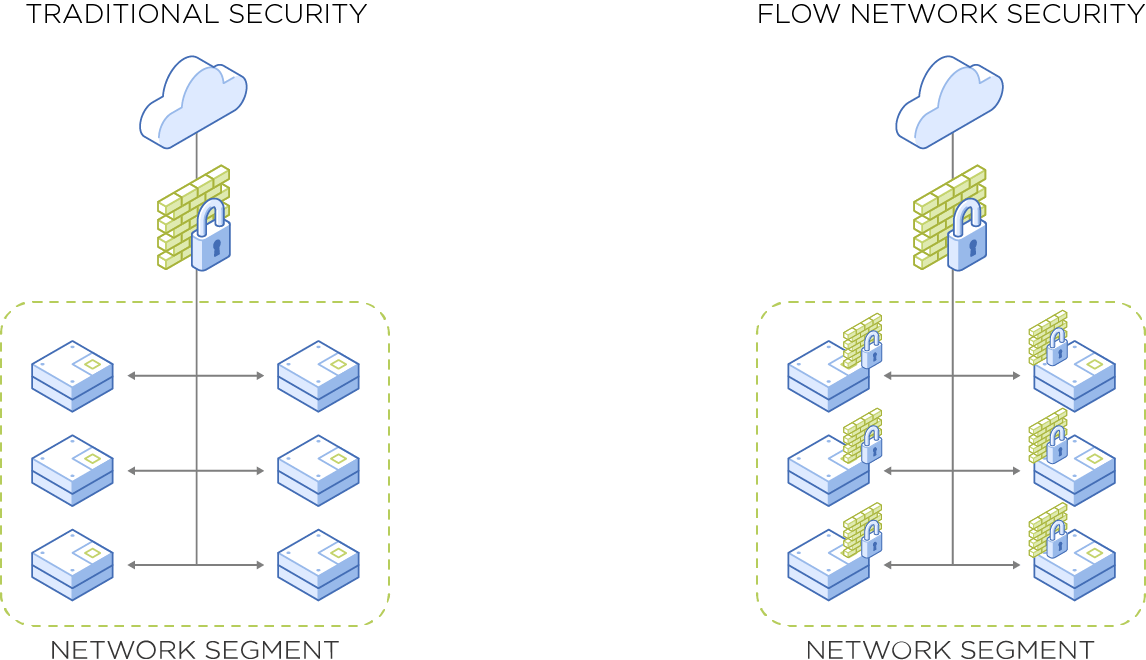
Software-defined firewalls for apps and data
Easily create Zero Trust-focused tagged firewalls to segment and protect your users, apps, and data from cyber threats without disrupting your current infrastructure.
Visibility to help comply and discover
Gain policy-defined visibility and insight into the communications and vulnerabilities of all your applications and services under one dashboard.
Network threat protection
Enable application tiering at the OSI L4 with the option to create deeper inspection at L7 using partner integrations built for Flow Network Security.
Increase Your Defence-In-Depth Strategy with Partner Integrations
Get to Know Flow Network Security
Nutanix is Trusted by 25,000+ Customers

"Flow Network Security is really focused on security, which is at the top of our mind. We have a very secure environment, but we’re always looking at ways to utilise technology to enhance that security. Flow Network Security enables us to follow an application all the way through and provide security wherever needed."
- Ken Shaffer, Assistant Vice President for Enterprise Systems, CarMax

"Micro-segmenting network policies for virtual machines and applications will give us a great level of control.” says Rout, “which we can apply through our Nutanix Prism console to reduce change management workloads."
- Dipak Rout, Head of IT, Arihant Capital Markets Ltd

"With its proven advantages in the manageability, scalability, disaster recovery, and simplified backups, Nutanix has played a vital role in helping us implement our ‘Internet + Innovative Talent Cultivation Plan.’ The highly efficient solution has ensured the stable operation of our smart teaching platform at a time when COVID-19 has made online teaching the new normal."
- Lin Nanhui, Director of the Network Centre, South China Normal University
Explore Our Cloud Network Security Resources

Application Centric Security Using Flow Network Security
Learn about Flow Network Security and how it works. Our tech note contains details on the Architecture, VM categorisation, and Policy Enforcement Types.

Flow Network Security Solution Brief
Quickly deploy a powerful software-defined security solution for critical workloads and data without additional complexity or management overhead.

Application Centric Security eBook
Learn more on how an application centric approach delivers the protection you need with more agility, flexibility, and above all, better security.