Organizations worldwide are in the midst of a massive wave of cybersecurity threats. Gartner reported that “ransomware families have grown by more than 700% in the last few years.” Every company is struggling to protect their data - the most important digital asset. As these attacks continue to mature both in frequency and intensity, their impact on business has grown exponentially. It is no longer something that happens to someone else; it is happening globally to both small and large organizations, indiscriminately, across all industries.

So, what are the implications? Imagine being a CIO of a hospital hit by a ransomware attack during a pandemic. The immediate impact is a major interruption in the ability to service patients, schedule appointments, retrieving patient records, and crippling all communication. The potential long-term impact is loss of sensitive patient data, loss of reputation, and of course loss of revenue.
Defense-in-Depth
There is no magic silver bullet that can prevent or insure against all ransomware threats. It is important to practice “defense-in-depth.” Defense-in-depth is a multi-layered approach to protect your data. Some of the defense mechanisms that you might consider include educating end users, carrying out regular vulnerability scanning, application whitelisting, role-based access control, and creating regular backups of your data. As important as these defense-in-depth techniques are, backups are your ultimate last line of defense and can restore your data after a cyber attack has already occured. Combining security best practices with sound backup and recovery planning can thwart costly cyber attacks. In this blog, we outline the capabilities of Nutanix and best practices that you can incorporate into your organization’s backup strategy for preventing and recovering from ransomware.
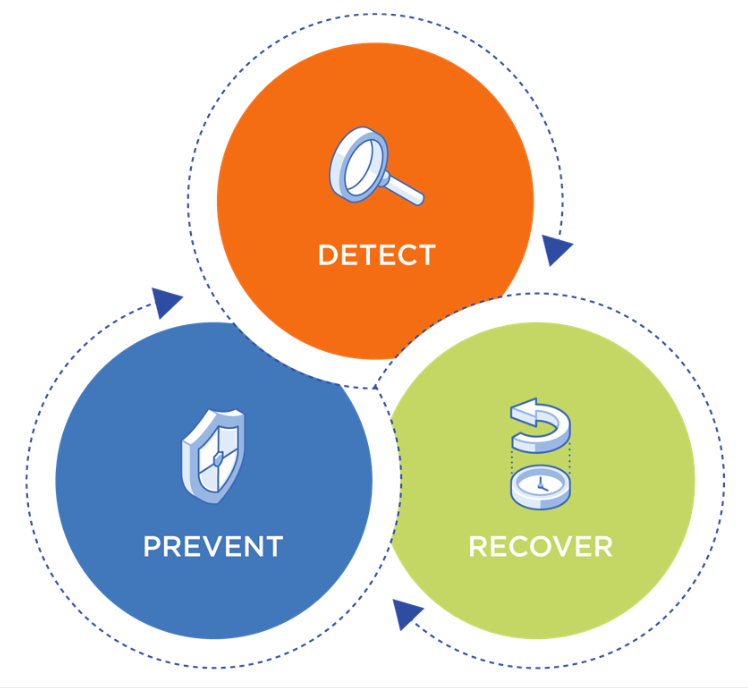
Ransomware protection has three aspects: prevention, detection, and recovery. Obviously, preventing a ransomware attack is ideal, but as attackers and tools become more sophisticated this is not always possible. In some attack forms, there might be a long lag between the actual infection and the activation of the malware. Detection algorithms are continuously enhanced and might be able to flag the malware before it gets activated. In the unfortunate case of an actual execution of malware, your company needs to be able to recover quickly to prevent costly downtime. Let’s look at some of the tools and best practices that you can leverage to protect your data.
1. Prevent
- Data Fabric Best Practices:
- Physical separation and segmentation of production networks and backup infrastructure network
- Apply the 3:2:1 backup methodology: three copies of your data on two separate media and one copy off-premises.
- Leverage an hyperconverged infrastructure (HCI) powered data protection platform such as Nutanix Mine to manage data backup and recovery. The Mine platform leverages the hardening (STIG, etc.) of standard AOS and AHV.
- Leverage Nutanix Mine for immutable storage by enabling WORM capabilities to “lock” backup copies for the specified period to prevent deletion or encryption of backups. Not even admin-access can delete or modify these backup copies. To learn more about the salient features of the Nutanix backup solution for rendering ransomware worthless, read an expert take here.
- Nutanix snapshots created on the production platform and leveraged for backups are read-only and immutable. Most backup solutions can leverage these snapshots for very quick (low RTO) restores of workloads, while still providing protection against most attacks.
- Day-to-Day Management Best Practices:
- Do not use default passwords; adhere to strong password policies
- Use multi-factor authentication when possible
- Use network segmentation to separate backup management traffic separated from production traffic
- Restrict access based on roles and user identities with RBAC
- Do not use Active Directory integration, but use local credentials for backup so AD attacks do not affect your data protection environment
- Don’t forget to look after your backup, they are your friend:
- Put in place regular backup schedules, and perform periodic reviews of backup policies
- Test your restores periodically to ensure your backup and recovery strategies are working properly to meet the intended SLAs, and your data is safe
- Keep backups of known-infected datasets for future analysis and detection
2. Detect:
- Leverage data protection tools to perform anomaly detection on backup sizes and traffic patterns
- Periodic (ideally automated) restore of workloads in a secure environment to perform antivirus and security scanning
- Use up-to-date security tools
- Log scanning for unauthorized access attempts
3. Recover:
- Rapid Recovery using Nutanix native snapshots
- Leverage the excellent performance of the Nutanix Mine platform to speed up restoration of backed-up workloads
These best practices will help your organization recover quickly and revert to secure clean copies of backups with minimal downtime and disruption to the business.
Data Protection Through Partnerships: Find Out More
Nutanix continues to cultivate a rich and highly specialized backup partner ecosystem to serve our customers’ growing needs for data protection. When software defined infrastructure meets software defined data protection, organizations can have confidence in the security and integrity of their data. See how Nutanix is combining the power of HCI with leading backup vendors to protect your data against ransomware.
Nutanix + HYCU: What happens when an inevitable Ransomware meets an immutable backup?
Nutanix + Veeam: Protect Backups from Ransomware with Nutanix and Veeam
Get Started Today!
Test Drive: Take a self-guided tour of Nutanix Mine, integrated data protection to protect your data at scale.
© 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.